Return of stolen cryptocurrency and blockchain investigation
We will conduct a detailed investigation to establish the location of the stolen cryptocurrency, block it and subsequently return it
We will explain and accompany the process of searching and returning funds from beginning to end
Why AML Crypto?
Own investigative tools
Our company has developed and successfully used special tools for conducting investigations. Own multi-chain transaction research tools and functionality for monitoring the movement of stolen funds.
Extensive experience with real refunds
A collected and researched database of fraudulent schemes and algorithms, hundreds of investigations every year and a large number of cases of the return of stolen funds.
Team of certified experts
Staff of certified anti-money laundering specialists, OSINT specialists and blockchain investigators.
We operate all over the world
Templates of legally correct documents for contacting law enforcement agencies, exchanges, exchangers and other participants in the chain of investigations. During the investigations, we interacted with more than 120 exchanges and crypto exchangers, 35 law enforcement agencies from different countries.
We provide free consultations and interviews
We conduct free interviews, provide consultations, add them to the scam database, and conduct an initial analysis of the flow of stolen funds.
Our reports are used by courts and police
Reports with the results of our investigations are used in judicial practice and in criminal cases. We work in various jurisdictions in compliance with the legal framework.
Examples of investigations

Example of Investigation #1

Example of Investigation #2

Example of Investigation #3

Example of Investigation #4
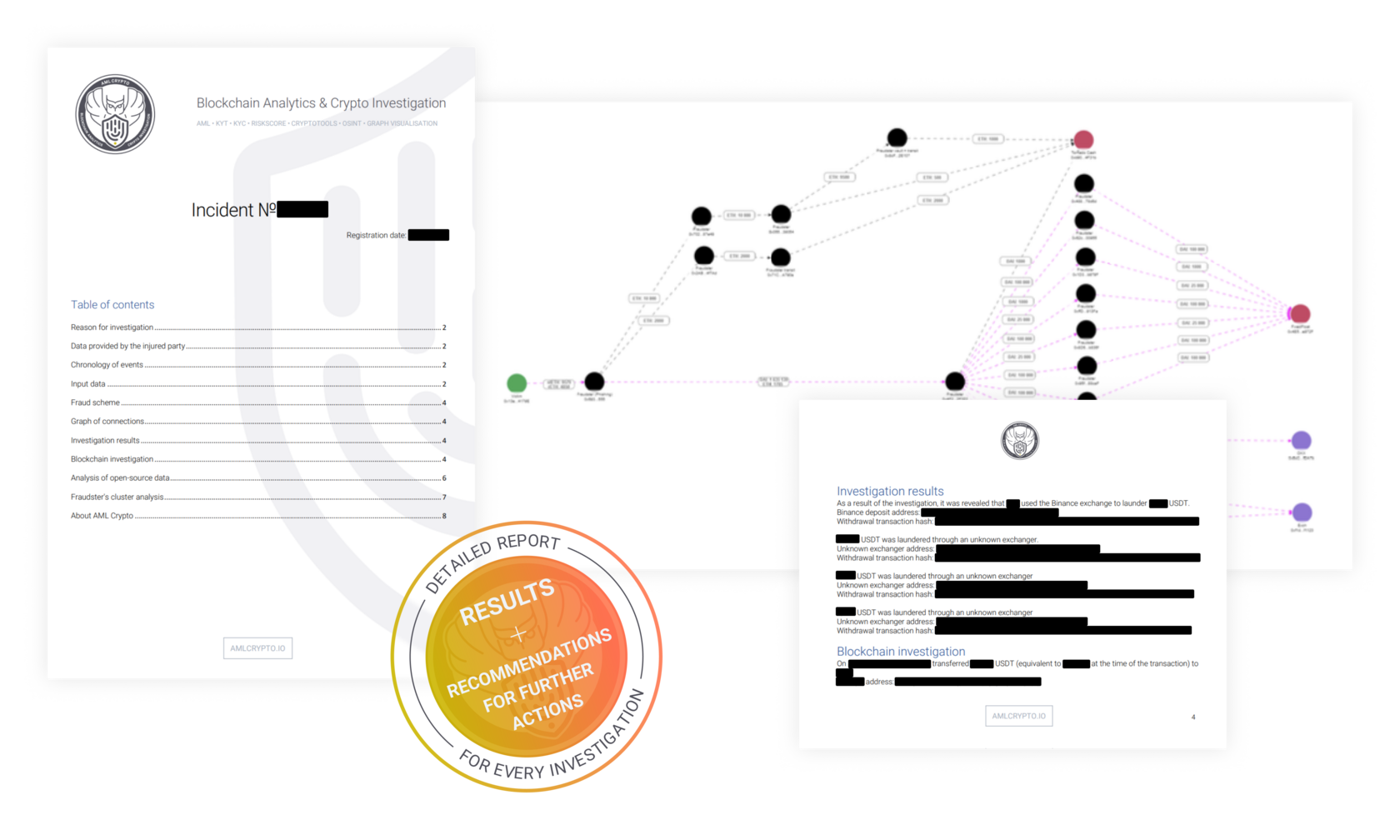
The process of searching and returning stolen cryptocurrency
What to do if your cryptocurrency is stolen?
Being specific and accurate in detail will help in future investigations or interactions with law enforcement.
Save all emails related to the fraudulent transaction, screenshots of messages from instant messengers and social networks, as well as any other possible evidence.
In the case of communication in Telegram, export the full chat in JSON format to extract the account ID — this information may be needed by specialists. If there were telephone conversations, take a photo of the call history. Record the names of the attackers’ websites and save payment receipts, especially if fiat funds were used. You need to act quickly: some data may be lost, and attackers may try to erase some information.
The information you collect will be very useful in providing incident details to relevant authorities and cybersecurity experts.
The blockchain is like an open ledger: every transaction is recorded. Knowing the user’s address, you can track where and how much money he sent. Using a blockchain browser, you can track the movement of funds.
If this process seems too complicated to you, you can contact professionals in specialized companies. They have tools that not only visualize the flow of funds, but also overlay markup on addresses, facilitating data analysis.
Stolen cryptocurrency funds are usually quickly converted into fiat money. To do this, scammers have a limited number of options available to them:
CEX (centralized crypto exchanges)
OTC P2P transactions (over-the-counter transactions between individuals)
ATM (cryptocurrency ATMs)
Stolen funds can travel through transit addresses, use blockchain bridges, and interact with smart contracts and mixers to make their movement more difficult to track.
The importance of receiving notifications of every movement of funds cannot be overstated, as this allows for a timely response, for example, if funds have arrived at the deposit address of the exchange.
If you don’t have enough knowledge, turn to blockchain investigation companies — it’s time to scrutinize every transaction and every address.
It is necessary to analyze the nature of the behavior of the funds, as well as the mention of related data on the Internet. This information should be organized in such a way that it is ready to be provided to law enforcement agencies and crypto exchanges. It is important to highlight key transactions, highlighting their hashes, and provide the data in a format that can be understood by any party that will assist in the return.
Here is key information to provide to law enforcement for follow-up requests:
- Phone numbers from which the attackers contacted you, along with the time and date of the calls. Despite the possibility of using temporary numbers, attackers can make mistakes.
- Site domain of scammers. Law enforcement agencies will be able to request information about the owner, IP logs and payment information from the domain registrar and hosting provider.
- Advertising platforms where you saw ads from scammers. As in the case of a domain, the attacker registered a personal account to launch advertising.
- Telegram-Username and Telegram-ID, if the communication was via Telegram, you can get a lot of useful information about the attacker… the groups he is a member of, his other messages, etc.
- Scammer profiles on social networks. Social networks collect extensive data about users, including logins, location, contacts and interests.
- Sites with reviews of scammers. Attackers often publish fake reviews about their fraudulent service, but in addition to “lies,” these reviews also contain digital clues about the user.
- Email addresses. Mail services store information about logins, locations, and devices used.
- Exchanges and crypto exchangers, which the attacker could use to launder funds. This information will allow law enforcement agencies to send requests for the provision of data under the KYC (Know Your Client) procedure.
Regardless of the location of the exchange, they do not seek to support illegal activities on their platform.
Most licensed exchanges actively cooperate with law enforcement agencies, blocking funds if fraud is suspected.
If you notice that your funds have been transferred to an exchange, please contact their technical support. Please note that a double application will be required: first in person or through a specialist, and then on behalf of law enforcement agencies.
The increase in the number of fraudulent schemes in the blockchain and the technical equipment of attackers increases the likelihood of losing crypto assets
